Database Hacking Using Sql Injection License
Web. Inspect. Introduction: With the exponential increase in internet usage, companies around the world are now obsessed about having a web application of their own which would provide all the functionalities to their users with a single click. In this quest for providing the customers with single click solutions, all the sensitive data is shifted on to a server which is then accessed by a web application. In most of the scenarios, web applications have direct access to the backend database and thus control valuable data. With a simple well crafted malicious payload a hacker can now get all the information from database. So it’s crucial that the web applications need to be secure enough to handle the attacks. Securing Web applications: It’s now apparent that securing web applications is essential for the companies to be in business. The real question is how it can be achieved.
- In today’s political climate, there’s a good chance you’re looking for less government-themed news, not more. However, if you’re looking for information.
- If database design is done right, then the development, deployment and subsequent performance in production will give little trouble. A well-designed database 'just.
Below are some of the checks that are in place to ensure that security holes in the web application are identified: Threat Modeling deals with identifying threats, attacks, vulnerabilities, and countermeasures for your application in the design phase. Security Code Reviews come into picture at the end of development phase. The entire code is inspected to find vulnerabilities. Manual Penetration Testing is done after the application is deployed in some environment. The application is attacked and assessed for vulnerabilities.
Automated Vulnerability Scanners are the tools which aid Penetration testers by identifying the vulnerabilities present. Web. Inspect is one of the most widely used automated vulnerability scanners in the market today. It helps us to identify vulnerabilities present in the web application by taking necessary input from us. IBM Appscan Standard Edition, Acunetix Scanner, Burp scanner, Nikto are the other vulnerability scanners that are in place. For the rest of this article I will be focusing on using Web.
Latest trending topics being covered on ZDNet including Reviews, Tech Industry, Security, Hardware, Apple, and Windows. Huy guyz i m hacker, ===== i sale tools and teach people how they can hack. 1:- credit cards 2:- bank log ins.
Inspect to identify security vulnerabilities. Web. Inspect: Web. Inspect is a web application security scanning tool offered by HP.

It helps the security professionals to assess the potential security flaws in the web application. Web. Inspect is basically a dynamic black box testing tool which detects the vulnerabilities by actually performing the attack. After initiating the scan on a web application, there are assessment agents that work on different areas of the application.
They report their results to security engine which evaluates the results. It uses Audit engines to attack the application and determine the vulnerabilities. At the end of the scan you can generate a report called . Using this report, client can fix the issues and then go for validation scanning to confirm the same. HP Web. Inspect is a commercial tool and you need license to scan a web site.
With the trail version you will be permitted to scan only zero. HP demo site). So Web. Inspect basically comes into picture when the application is hosted in some environment (test/QA/production).
As with every other tool there are both advantages and disadvantages associated with using Web. Inspect. Advantages: Saves time when dealing with large enterprise applications. Simulates the attack, shows the results and presents you with a comprehensive view. It is not dependent on the underlying language. Disadvantages: It’s hard for any tool to find logical flaws, weak cryptographic storage, severity of the disclosed information etc. It has a list of payloads that it uses on every web application. It does not use any wisdom in generating payloads depending on the type of application.
There could be false positives among the listed vulnerabilities. Having said that, Web.
Inspect scores high on many features and helps a great deal in providing scanning solutions. Main Features in Web. Inspect 9. 1. 0: Web. Inspect 9. 1. 0 is the latest version in use as of today. Below lines would throw an insight into various features that are available in Web. Inspect. Presents you with tree structure: By crawling the entire application Web.
Inspect presents you with the hierarchical tree structure of the web application and lists all the available URLS. Customizable Views: While viewing the results of a scan Web. Inspect offers different views as per your requirement. Scanning Policies: Web. Inspect gives you the freedom to edit and customize the scanning policies to suit your requirements and thus offers great flexibility.
Manual Hacking Control: With this option you can actually simulate an attack environment and see what’s really going on during a particular attack. Report Generation: You can generate customizable reports by including desired sections and in desired format. Remediation: Web. Inspect would provide a summary and the necessary fixes required to fix the vulnerabilities detected during a particular scan. Web Services Scan: Web services usage is growing at a rapid pace. You can assess web service vulnerabilities by using Web. Inspect. Tools: There are lot many tools that come with Web.
Inspect like web proxy, SQL Injector, web fuzzer, web macro recorder etc. We will now move into the actual scanning part and will explore the tool and its features. Activex Software Development Kit Sdk Documentation. Installation Part: Before you install Web. Inspect make sure that the system has at least 2 GB RAM and Microsoft SQL Server installed. After installation, the first time you start Web. Inspect it will open the .
If you don’t have one you can go for a 1. Figure 1. Depending on the scanning policy selected, Web.
Inspect will try to attack the web application which can harm the server. It sends many HTTP requests which results in increased traffic. So make sure that you keep these things in mind and accordingly conduct the scan. THE TWO “C+A”s: Two things that Web.
Inspect will do for you: Crawl + Audit. Two things that you need to do for Web. Inspect: Configure + Analyze. Crawl: Crawling is the process by which Web. Inspect will build the tree structure of the entire website by traversing every possible link on that site.
Audit: Auditing is the process of performing attacks to assess the vulnerabilities. Crawl + Audit = Scan. Configure: You need to tell the Web.
Inspect what you need from it. If you do not want it to hit a particular functionality in your site you need to specify that before hand or if you are bothered to find out only about XSS & SQLi vulnerabilities you need to mention the same to Web. Inspect. So configuring is basically letting the Web. Inspect know what you want and what you do not want. This is especially done in the . So select Website scan.
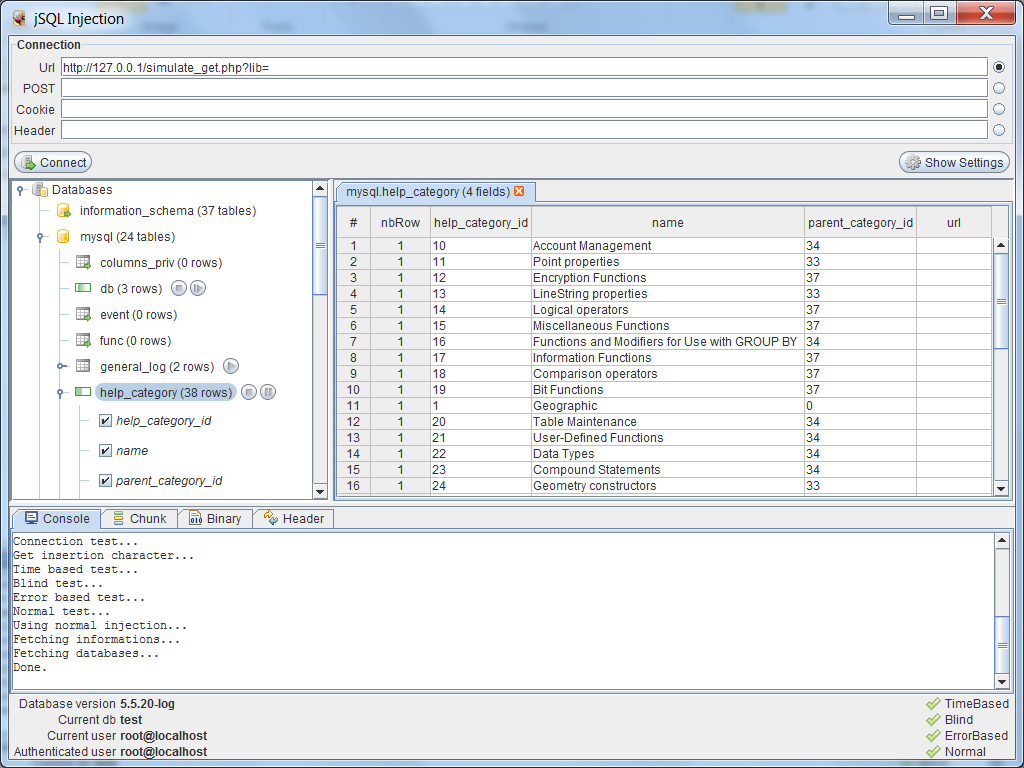
In the scan wizard, on the right hand side you can see the recently opened scans and the scans that are in schedule. You can also schedule a scan to begin at a particular time. Figure 2. Upon selecting the website scan you will be taken to the below window (Figure 3) where you need to enter the scan name. It is standard way to start a scan.
List Driven scan: Allows you to specify the list of URL’s that are to be scanned. Only those URLs will be scanned. The URL’s can be specified in a text file.
Workflow Driven scan: This is used to scan only a part of your site not the entire site. The part that needs to be scanned can be specified by a workflow macro which we will be looking into soon. Manual scan: Allows you to manually specify the links that are to be scanned by browsing through them in the step mode.
Below the standard scan you can see restrict to folder option which defines the scan coverage. This is very important as the scan coverage depends on the option that you select. The following are the options you can choose from the dropdown list: Directory only: If you select this option and specify a URL say www. Mysite/Myfolder/Mypage. Web. Inspect will assess only Myfolder and not the directories present inside it.
Directory and sub directories: Web. Inspect will not hit any folder that is higher in the directory tree.
Directory and parent directory: Web. Inspect will not hit any folder that is lower in the directory tree.
Ten Common Database Design Mistakes. No list of mistakes is ever going to be exhaustive. People (myself included) do a lot of really stupid things, at times, in the name of “getting it done.” This list simply reflects the database design mistakes that are currently on my mind, or in some cases, constantly on my mind.
I have done this topic two times before. If you’re interested in hearing the podcast version, visit Greg Low’s super- excellent SQL Down Under. I also presented a boiled down, ten- minute version at PASS for the Simple- Talk booth.
Originally there were ten, then six, and today back to ten. And these aren’t exactly the same ten that I started with; these are ten that stand out to me as of today.
Before I start with the list, let me be honest for a minute. I used to have a preacher who made sure to tell us before some sermons that he was preaching to himself as much as he was to the congregation. When I speak, or when I write an article, I have to listen to that tiny little voice in my head that helps filter out my own bad habits, to make sure that I am teaching only the best practices. Hopefully, after reading this article, the little voice in your head will talk to you when you start to stray from what is right in terms of database design practices.
So, the list: Poor design/planning Ignoring normalization Poor naming standards Lack of documentation One table to hold all domain values Using identity/guid columns as your only key Not using SQL facilities to protect data integrity Not using stored procedures to access data Trying to build generic objects Lack of testing. Poor design/planning “If you don’t know where you are going, any road will take you there” – George Harrison. Prophetic words for all parts of life and a description of the type of issues that plague many projects these days. Let me ask you: would you hire a contractor to build a house and then demand that they start pouring a foundation the very next day? Even worse, would you demand that it be done without blueprints or house plans? Hopefully, you answered “no” to both of these. A design is needed make sure that the house you want gets built, and that the land you are building it on will not sink into some underground cavern.
If you answered yes, I am not sure if anything I can say will help you. Like a house, a good database is built with forethought, and with proper care and attention given to the needs of the data that will inhabit it; it cannot be tossed together in some sort of reverse implosion. Since the database is the cornerstone of pretty much every business project, if you don’t take the time to map out the needs of the project and how the database is going to meet them, then the chances are that the whole project will veer off course and lose direction. Furthermore, if you don’t take the time at the start to get the database design right, then you’ll find that any substantial changes in the database structures that you need to make further down the line could have a huge impact on the whole project, and greatly increase the likelihood of the project timeline slipping. Far too often, a proper planning phase is ignored in favor of just “getting it done”.
The project heads off in a certain direction and when problems inevitably arise – due to the lack of proper designing and planning – there is “no time” to go back and fix them properly, using proper techniques. That’s when the “hacking” starts, with the veiled promise to go back and fix things later, something that happens very rarely indeed. Admittedly it is impossible to predict every need that your design will have to fulfill and every issue that is likely to arise, but it is important to mitigate against potential problems as much as possible, by careful planning. Ignoring Normalization Normalization defines a set of methods to break down tables to their constituent parts until each table represents one and only one “thing”, and its columns serve to fully describe only the one “thing” that the table represents. The concept of normalization has been around for 3. SQL and relational databases are implemented.
In other words, SQL was created to work with normalized data structures. Normalization is not just some plot by database programmers to annoy application programmers (that is merely a satisfying side effect!)SQL is very additive in nature in that, if you have bits and pieces of data, it is easy to build up a set of values or results. In the FROM clause, you take a set of data (a table) and add (JOIN) it to another table. You can add as many sets of data together as you like, to produce the final set you need. This additive nature is extremely important, not only for ease of development, but also for performance. Indexes are most effective when they can work with the entire key value. Whenever you have to use SUBSTRING, CHARINDEX, LIKE, and so on, to parse out a value that is combined with other values in a single column (for example, to split the last name of a person out of a full name column) the SQL paradigm starts to break down and data becomes become less and less searchable.
So normalizing your data is essential to good performance, and ease of development, but the question always comes up: “How normalized is normalized enough?” If you have read any books about normalization, then you will have heard many times that 3rd Normal Form is essential, but 4th and 5th Normal Forms are really useful and, once you get a handle on them, quite easy to follow and well worth the time required to implement them. In reality, however, it is quite common that not even the first Normal Form is implemented correctly. Whenever I see a table with repeating column names appended with numbers, I cringe in horror. And I cringe in horror quite often. Consider the following example Customer table: Are there always 1. Download The Pacific Subtitle Indonesia Descendants.
Is the order of payments significant? Does a NULL value for a payment mean UNKNOWN (not filled in yet), or a missed payment? And when was the payment made?!?
A payment does not describe a Customer and should not be stored in the Customer table. Details of payments should be stored in a Payment table, in which you could also record extra information about the payment, like when the payment was made, and what the payment was for: In this second design, each column stores a single unit of information about a single “thing” (a payment), and each row represents a specific instance of a payment. This second design is going to require a bit more code early in the process but, it is far more likely that you will be able to figure out what is going on in the system without having to hunt down the original programmer and kick their butt. If everyone agreed that, from now on, a rose was going to be called dung, then we could get over it and it would smell just as sweet. The problem is that if, when building a database for a florist, the designer calls it dung and the client calls it a rose, then you are going to have some meetings that sound far more like an Abbott and Costello routine than a serious conversation about storing information about horticulture products. Names, while a personal choice, are the first and most important line of documentation for your application.
I will not get into all of the details of how best to name things here- it is a large and messy topic. What I want to stress in this article is the need for consistency. The names you choose are not just to enable you to identify the purpose of an object, but to allow all future programmers, users, and so on to quickly and easily understand how a component part of your database was intended to be used, and what data it stores. No future user of your design should need to wade through a 5. Consider, for example, a column named, X3. What the heck does that mean?
You might decide, after some head scratching, that it means “X3. Possibly it does, but maybe DSCR means discriminator, or discretizator?
Unless you have established DSCR as a corporate standard abbreviation for description, then X3.